What is Web Application Firewall ( WAF )?
A web application firewall (WAF) is a security layer that can work with your web server or in front of your web server that monitors and filters incoming traffic to the web application. The duty of the WAF is to block malicious traffic, and bots while allowing legitimate traffic through. With a proper WAF, you may eliminate most of the web security threats against your websites or web applications and can avoid compromised websites on your server.
Importance for Web Application Firewall in DirectAdmin
The actual duty of WAF is to secure websites/web applications from web attacks and malicious access. On a DirectAdmin server where people normally host multiple websites, thus a security layer like WAF is essential because there must be multiple types/versions of web applications and frameworks installed on the same server. On many such servers, the installed Web Applications may contain known or unknown vulnerabilities which are the key for hackers to gain access to the website or the user account. With a proper Web Application Firewall, we can stop most of such website vulnerability scanners, general web attack attempts, and website compromise, and eventually helps to reduce server load/overhead and save server admin time. It is easy to enable and manage cPGuard WAF on a DirectAdmin server we provide complete support for the integration and log management.
cPGuard WAF
The cPGuard WAF is powered by Malware.Expert Commercial ModSecurity rules set and tuned for shared hosting servers. It is written from scratch based on the real-world analysis of websites for over 10 years and can block most generic and targeted attacks. It can block most of the generic attacks against Web Server and PHP, broken out into the following attack categories:
- SQL injection
- Cross-site Scripting (XSS)
- Local File Include
- Remote File Include
- File upload vulnerabilities
- Zero-Day attacks
- Web shells executions
- Captcha verification
It also has optimized application-specific Mod_Security rules, covering the same vulnerability classes for applications such as:
- WordPress
- Joomla
- Drupal etc
How cPGuard WAF can help to block web attacks and reduce server load?
The cPGuard WAF has various rules set, which you can enable optionally based on your preference. The rules together can stop bad bot access, completely stop WordPress login page/ xmlrpc.php attacks using the unique captcha system, and block generic attacks.
For example, you may not need to worry about SQL injection attacks after enabling cPGuard WAF. This is a major issue, especially for WordPress plugins where such vulnerabilities are reported quite often ( recent examples are CVE-2023-23488, CVE-2023-23489, and CVE-2023-23490 ). You can be worry-free and do not need to follow it and force the users to patch them to avoid a compromised website.
How to enable cPGuard WAF?
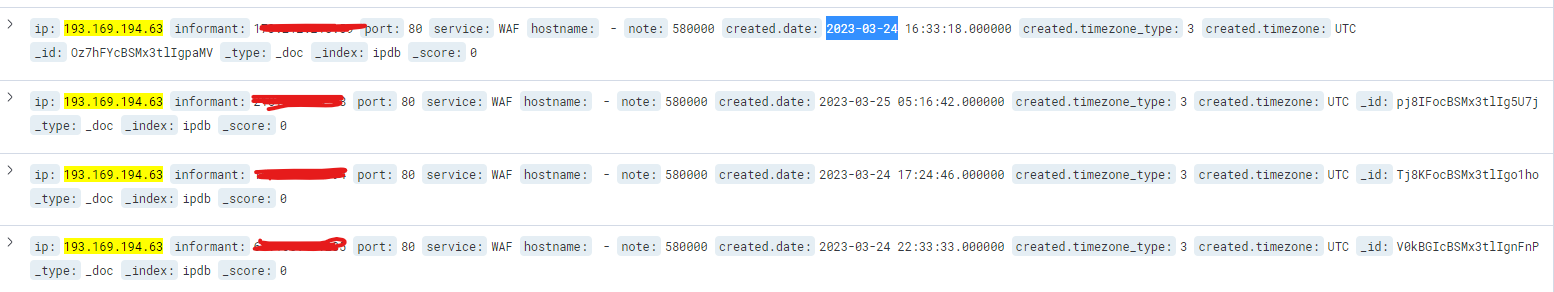
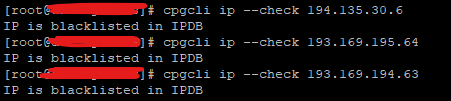
To install and enable cPGuard WAF, you may need to purchase and install cPGuad first on your server. After installing cPGuard on your server, you may refer to this help article and enable WAF on your server. It is easy to enable – disable WAF with a few clicks. You also have the flexibility to enable/disable selective WAF rules set for specific types of attacks. You can view the WAF logs from App Portal and each user can view the web attacks against their websites from their user plugin available in DirectAdmin.
Conclusion
The cPGuard WAF is the cost-effective and efficient WAF and Security Plugin available now for your DirectAdmin server. It is compatible with all web servers supported in DirectAdmin and enables seamless integration with them. The cPGuard WAF can automate malware scans, web attack mitigation, and distributed attacks, and can help to reduce server load and total time to manage servers. We have 30 days free trial using which you can try the solution without payment…it is also the cheapest security suite even after the trial period.