Injecting bad code into a legitimate file or inserting a bad file into an application folder is a very common type of virus attack. But there are some specific cases where repeated file injection happens to the same file or folder. In such cases even if the scanner detects and take action against the detected instance, it may happen again and causes a scanner log flood. In this blog, we are discussing some common reasons that can cause such issues based on the cases that we handled in the past.
1. Cron Jobs
This is a very common type of cause for repeated file injections and is easy to find. In this scenario, the user account is compromised and the attacker is taking advantage of it to install malicious cron jobs to repeatedly inject files into the account.
Given below is an active campaign specifically targeting to cPanel account, where the compromised cPanel accounts through some campaign are being abused with similar cron jobs for the past couple of weeks.
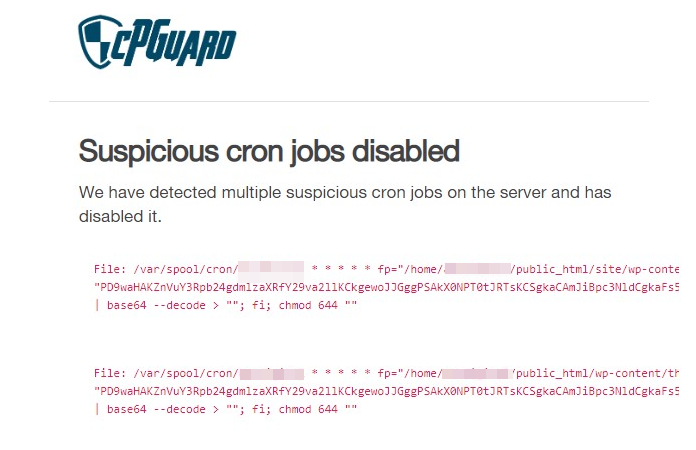
There can be other types of cron jobs as well, which will download the file from a remote location and execute it. This will run as a daemon on the server which will monitor and upload/update malicious code into the account.
2. Process or Daemon run under the user account
This type of abuse is also common and a bit more aggressive than the scheduled cron-based injections. As it is a running process, it actively tracks any change to the targeted infected file or location and adds infection if it cannot find the bad code in it. This type of abuse is easy to find because the bad process keeps running and consumes resources. You can easily track such jobs by listing the processes owned by the affected user using “ps” command. Few such examples are given below…
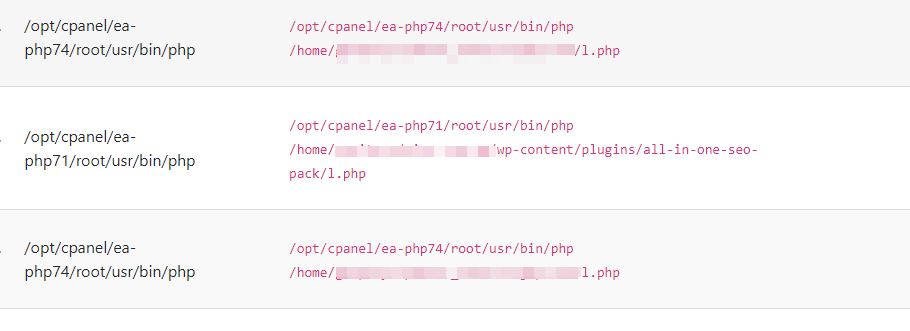
cPGuard has a process monitoring module integrated, which will peridiocally scan the processes running under the user accounts, take action and report them if matches to any of the known abuse patterns.
3. Using hidden code in nulled third-party modules
This is another method and is difficult to find because it needs source code verification of all files within the account. This often happens with nulled WordPress plugins/themes which the users often install to save some money. But such packages will cause more damage and can ultimately turn your website not unable and vulnerable. You need to go through each files or use a malware scanner like cPGuard to find such hidden malicious code. An example for such case is given below, which will run every time you access th website and include malcious code into the index.php file
Conclusion
The reason for repeated file infection is not just limited to this but can happen due to other reasons as well. But these are the most common reason behind repeated infections and cPGuard is being trained to handle many such cases already. But ultilamtely it is required to find the security hole using which the hacker got access to the account and patch it. Otherwise the attacker can come back any time and repeat the action.

