In cPGuard, you have the option to stop uploading PHP scripts through the Web, which includes a web form, web file managers, and web shells. Please note that this option will disable all types of PHP script uploads through Websites and thus should be aware that you cannot edit and save PHP files using the Web. Once this option is enabled, you should use FTP, SSH, Control Panel File Manager, etc to upload and update PHP scripts to your websites.
To enable the option you have 2 options.
1. Using CLI
You can enable PHP script upload blocker in WAF using the following command
cpgcli upload-scanner --block-php=enableTo revert this setting, you can use the following command.
cpgcli upload-scanner --block-php=disable2. Using App Portal Setting
Log in to App Portal > Choose your server > Go to Settings > Additional Settings > Turn ON the option “Block PHP files upload “
To revert the action, you can turn off the switch
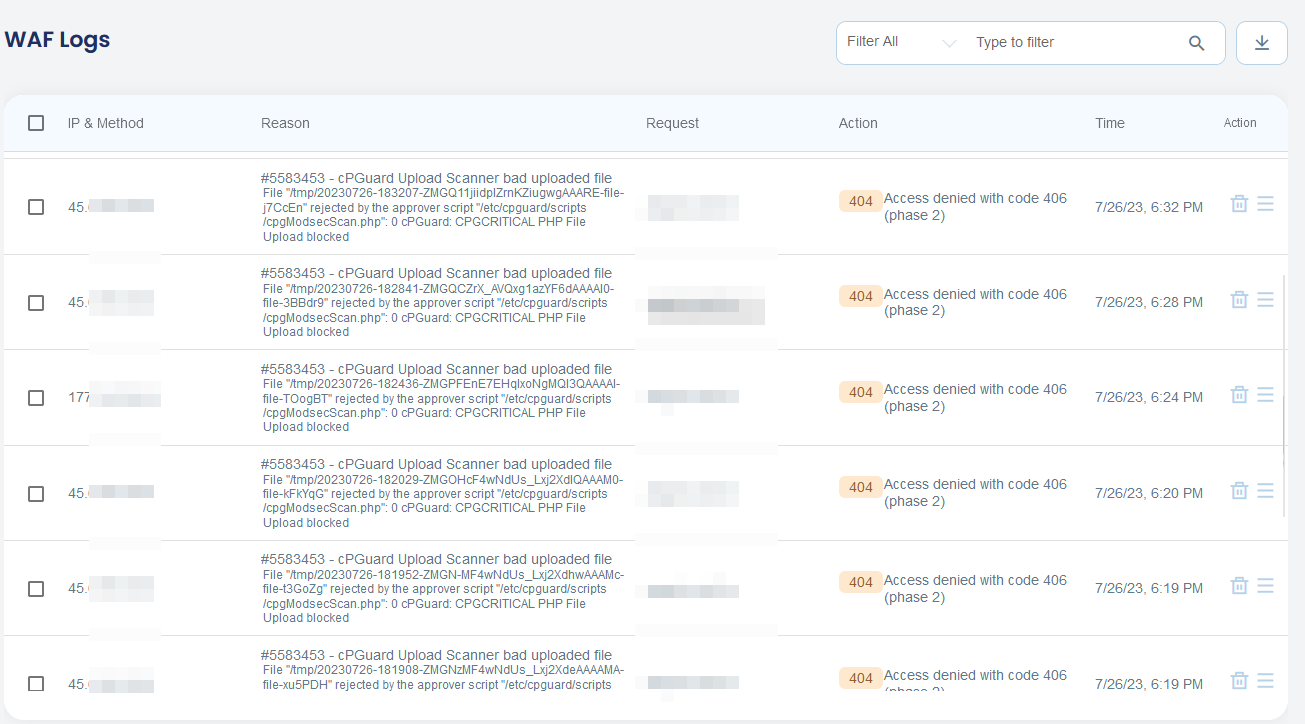
How to verify that it is working?
Once the PHP script upload is enabled in WAF, you can notice an entry like the following in WAF Logs each time it blocks PHP script uploads