You have options to report files for our review in case
- you suspect that the reported file(s) by the scanner as a virus is a legitimate file
- if cPGuard scanner engine does not identify a virus file
In both of the above cases, we have to access the file contents and analyze the code to make necessary modifications in the scanner engine. You may use the following options to report the files to us
1. Report a false positive
You can report a file as a false positive from the App Portal or using CLI.
From the App Portal, go to the scanner logs, locate the file to report, click on the file details icon on the right side, and click on the “Report False Positive” button in the pop-up menu on the right side of the page. Please refer the given image below.
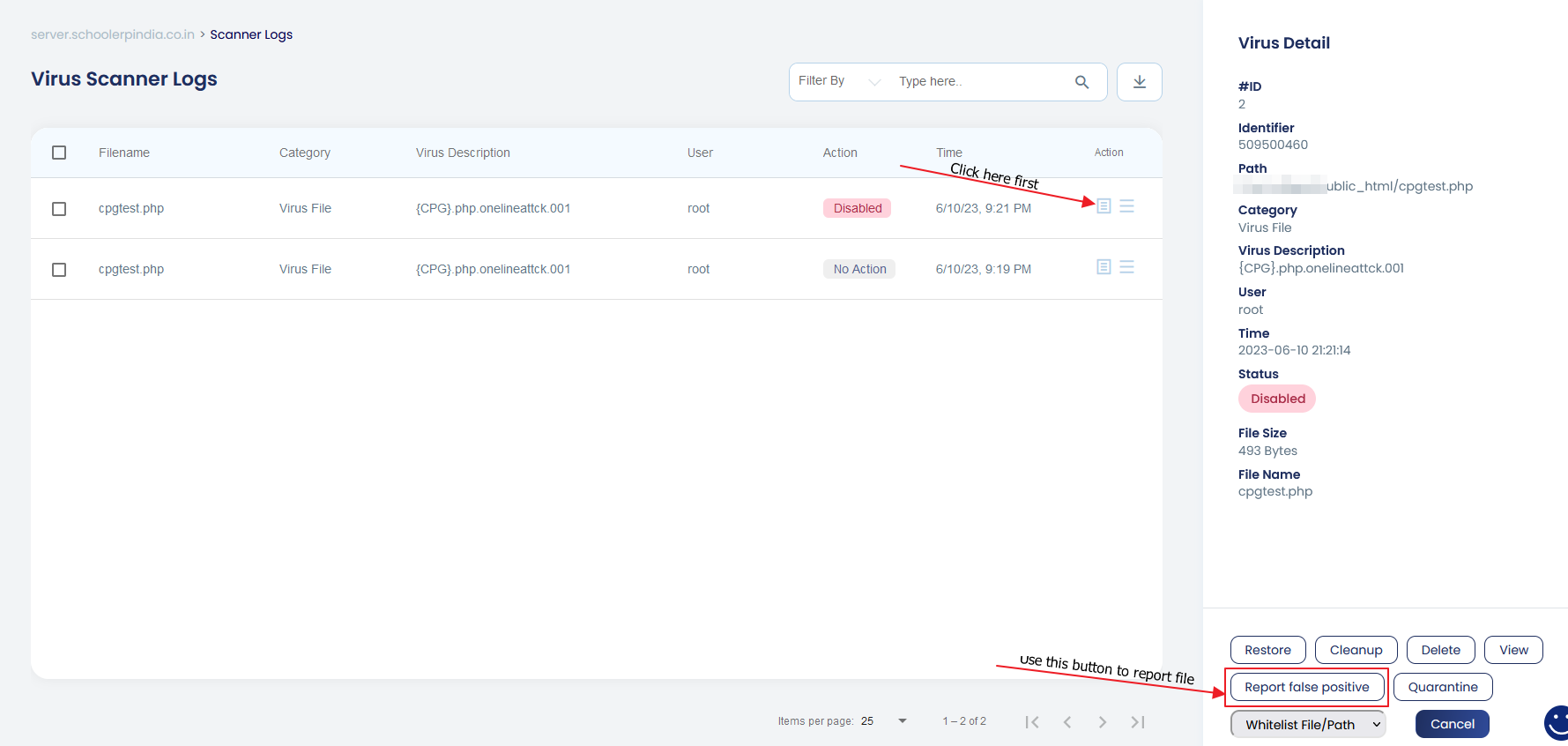
You can also report the false positive using CLI with the following command. Here make sure that the <file path> is the exact location of the file on your server ( in quarantine or the actual path in the user account )
cpgcli report --false-positive <file path>2. Report a virus file
Like any other scanner engine, the cPGuard scanner also works based on how it is trained with the virus samples. If cPGuard scanner is not reporting a virus file after the files scan, you may report the particular virus file to us so that we can check, analyze and update the scanner engine to detect similar files in the future.
You can use the following command to report a virus file for our review
cpgcli report --virus <file path>Any such sample reporting, feedback, and any similar inputs will help us to improve cPGuard and offer better protection in each updates.
