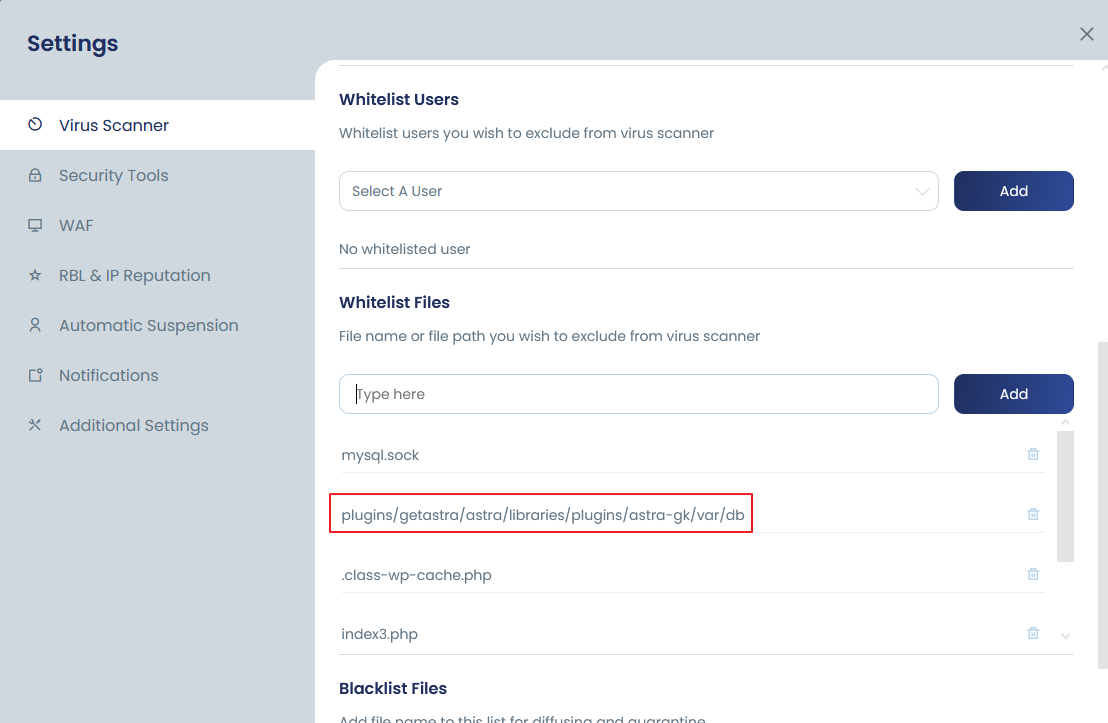
Whitelist files
In cPGuard, there are multiple options to whitelist certain entities from the scanner reports. You can
- Whitelist a file name
- Whitelist a file path ( specific cases )
- Whitelist the relative file path
Whitelist a file name
This option helps in case you wish to whitelist a specific file name. We recommend not whitelist file name which is common ( like index[dot]php ) or flagged as malicious already ( like wp-vcd[dot]php ]. To activate this, go to cPGuard >> Settings >> Scanner:- Into the “Whitelisted Files”, add your file name. This will be active instantly for the automatic scanner.
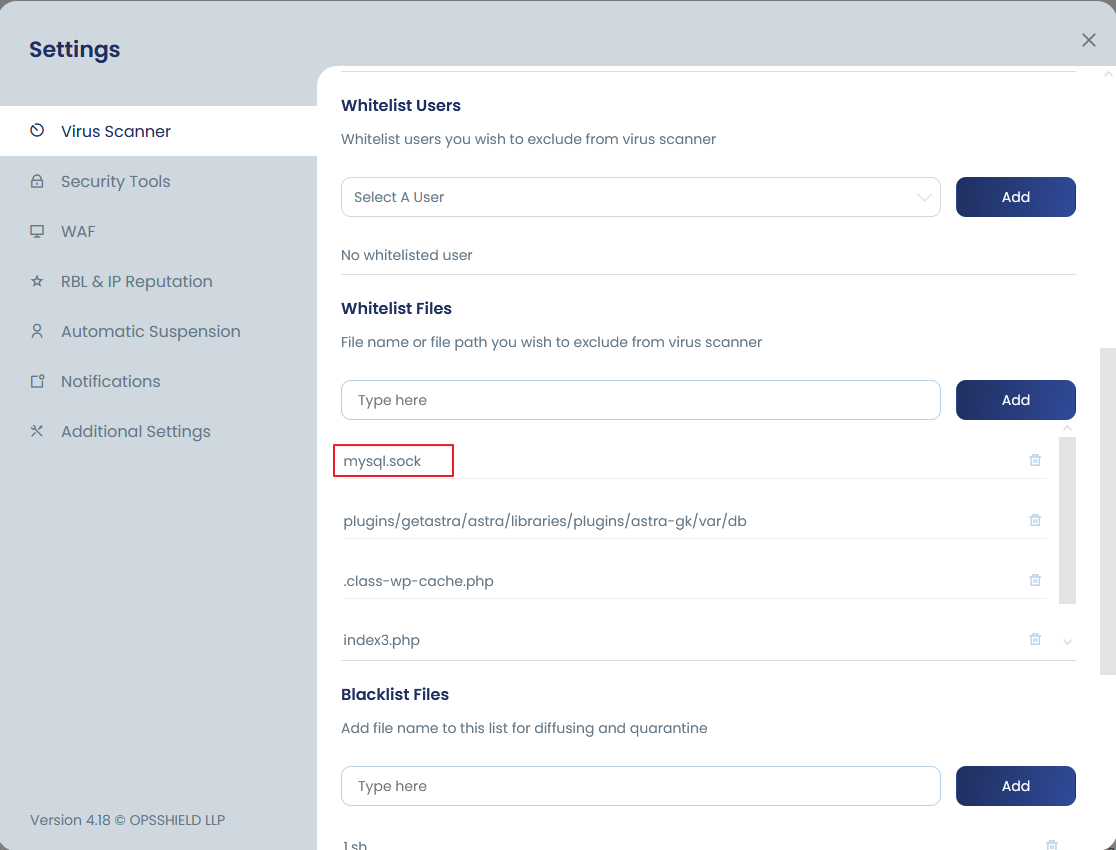
Whitelist a file path
This option is helpful especially when you wish to whitelist a specific file location. This is more safe compared to whitelisting a file name because it will match the exact location. To whitelist a file path, go to cPGuard >> Settings >> Scanner:- Into the “Whitelisted Files”, add your file path. This will be active instantly for the automatic scanner.
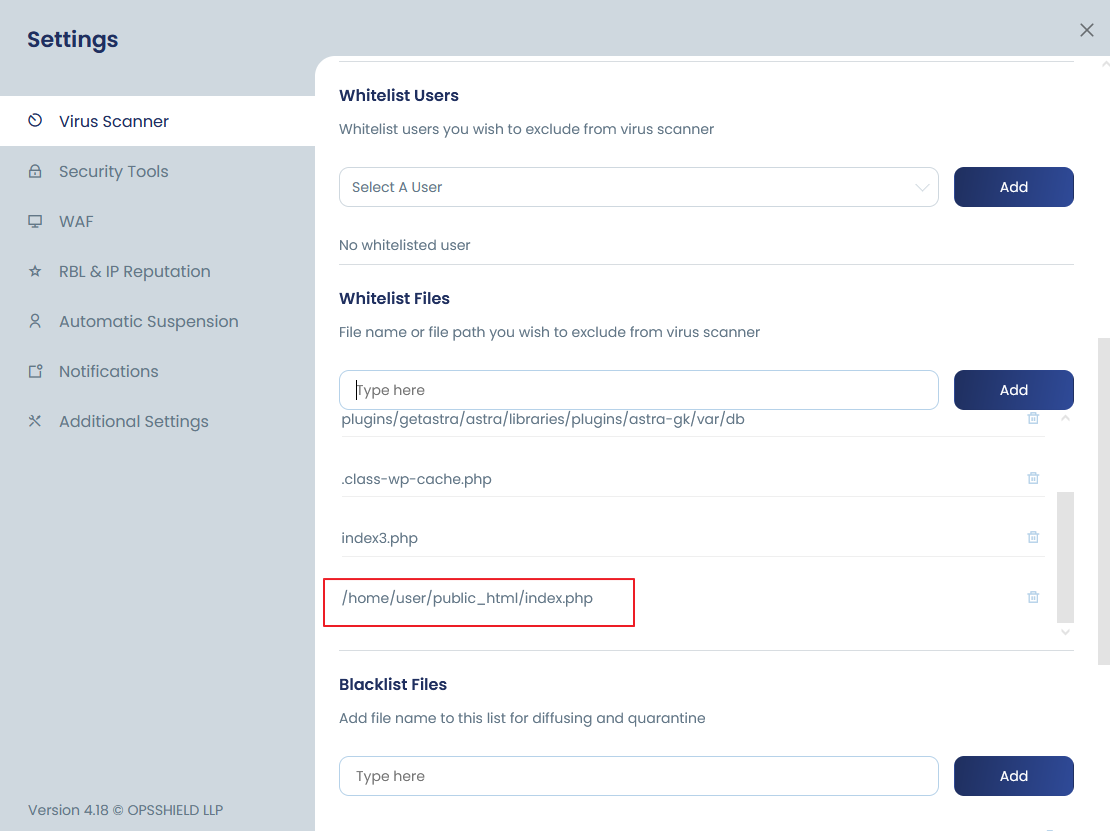
Whitelist a relative file path
This option will help to whitelist files in a more generic way and can optionally help to whitelist directories. To add this whitelist, go to cPGuard >> Settings >> Scanner:- Into the “Whitelisted Files”, add your file path string. This will be active instantly for the automatic scanner.
For example: to whitelist a directory like “/home/user1/public_html/dir/exclude” – you can whitelist either of the following entries
1. Full path like “/home/user1/public_html/dir/exclude/”
OR
2. Partial path like “user1/public_html/dir/exclude/”
NOTE :- If you add “/home/user1/public_html/dir/exclude” that will also whitelist “/home/user1/public_html/dir/exclude1” as well. So make sure to add exact string like “/home/user1/public_html/dir/exclude/”