Skip to main content
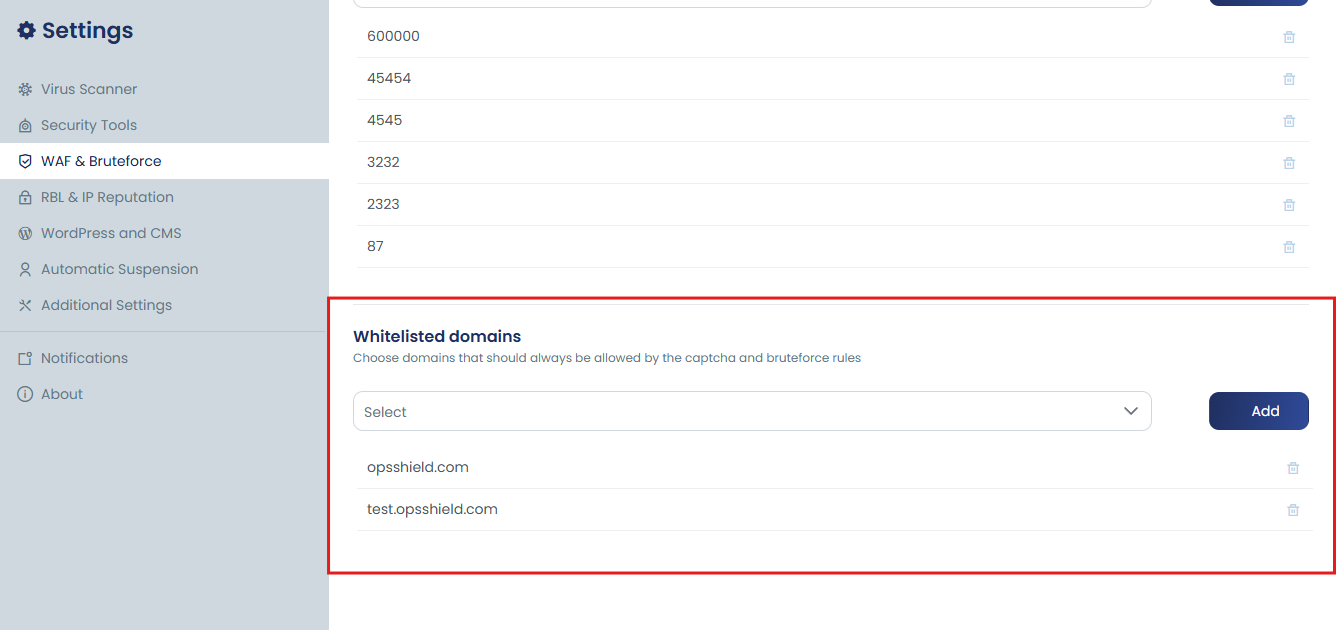
cPGuard does provide an option to whitelist your domains from brute-force protection checks. We strongly recommend you to avoid whitelisting unless the domain is protected using some other security means.
To whitelist a domain Go to App Portal cPGuard >> Settings >> WAF & Bruteforce:- There you can find the section “Whitelisted Domains”. Click the input box, select domain name then click Add.

