cPGuard WAF is a set of ModSecurity rules set which can work with Apache, Nginx, and Litespeed Web Servers. As it is written on top of the ModSecurity module, it has related dependencies and they must meet before enabling cPGuard WAF. Based on the control panel and other software you use on your server, you may need to adjust related settings to make things ready for cPGuard WAF.
Here we will describe some of the common and generic settings that you need to do if you are getting WAF settings errors in cPGuard
Requirements and Settings
The server must meet the following requirements to enable cPGuard WAF
- ModSecurity version 2.9.4 or higher must be enabled on the Web Server
- SecRuleEngine should be turned ON
- OWASP rules set must be DISABLED as it is not compatible with our WAF
- SecAuditLog must be enabled to display WAF logs in the UI [ not required WAF to block attacks…it is only for logging purposes]
Settings in cPanel
The following values should be set properly in Home >> Security Center >> ModSecurity™ Configuration » Configure Global Directives
- “Audit Log Level SecAuditEngine” should be set to “Only log noteworthy transactions” which is recommended
- “Rules Engine SecRuleEngine” should be set to “Process the rules”
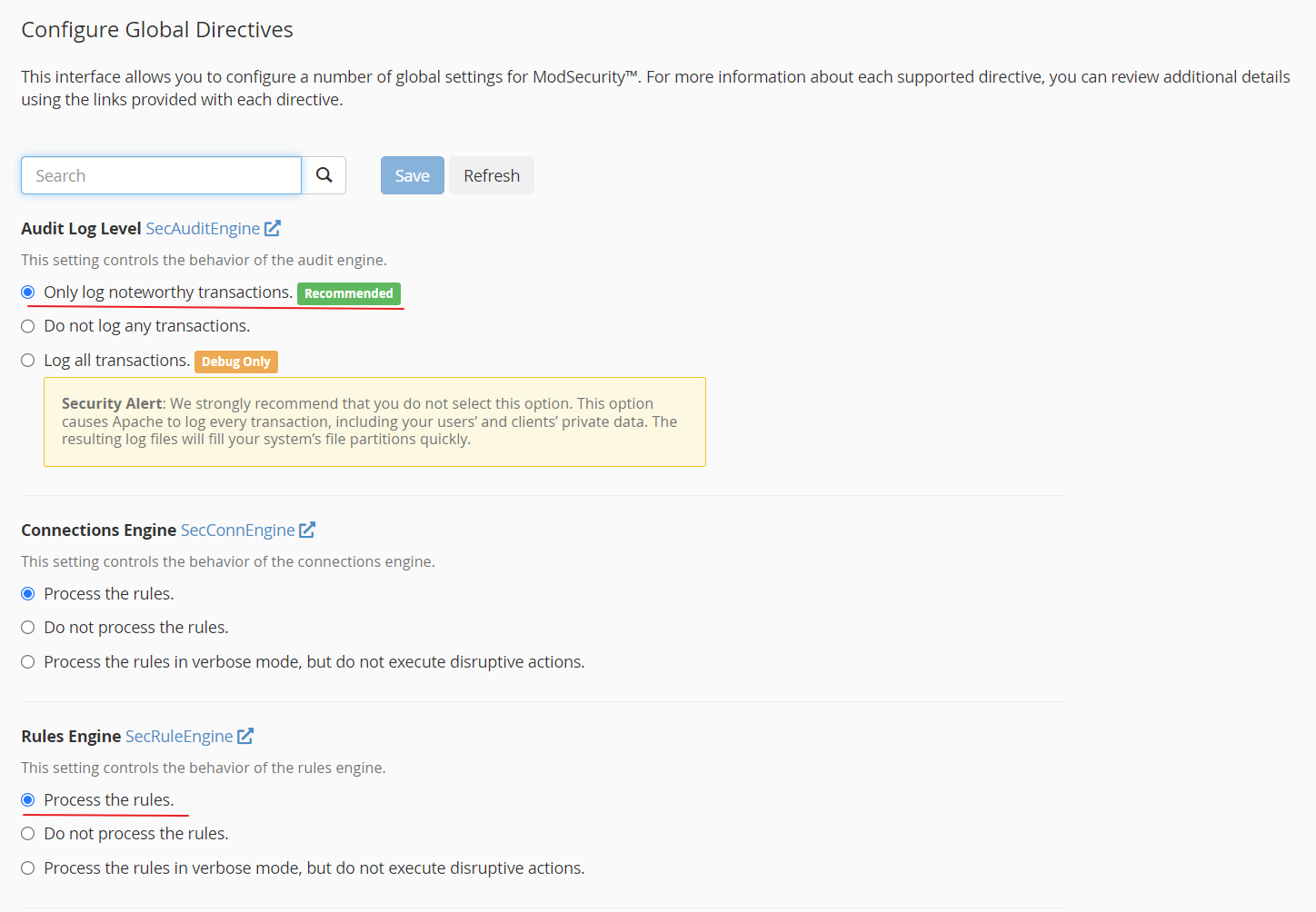
Also do not enable additional ModSecurity vendor rules from WHM >> Security Center >> ModSecurity™ Vendors » Manage Vendors
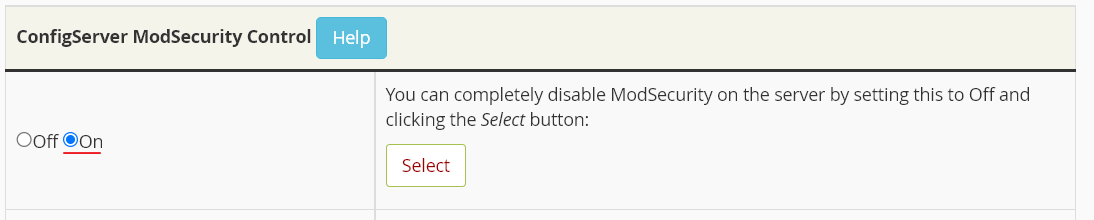
ConfigServer ModSecurity Control
You should not turn off ModSecurity in ConfigServer ModSecurity Control [ CMC ]
Settings in DirectAdmin
You should enable ModSecurity in your Web Server without any additional rules. The CWAF rules are compatible and you can enable that optionally if you would like.
cd /usr/local/directadmin/custombuild
./build update
./build set modsecurity yes
./build set modsecurity_ruleset "no"
./build modsecurity
./build modsecurity_rules
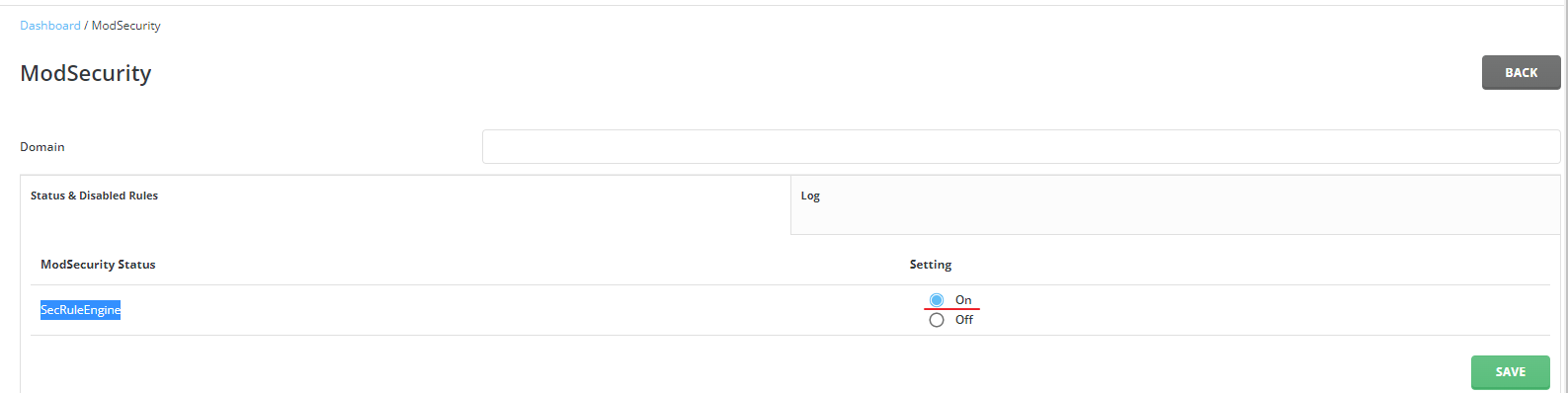
./build rewrite_confsYou should also make sure that SecRuleEngine is enabled in SecRuleEngine should be ON from DirectAdmin >> Server Manager >> ModSecurity
Plesk ModSecurity Settings
In Plesk, you need to enable ModSecurity module in Apache or Nginx with our custom rules set or Comodo WAF ( based on your preference ) before enabling WAF. Please note that you should not enable OWASP rules set, as it is not compatible with cPGuard WAF.
The recommended ways to enable ModSecurity before turning on cPGuard WAF are given below
If you wish to enable ModSecurity in Apache, run following command
plesk bin server_pref --update-web-app-firewall -waf-rule-engine on -waf-web-server apache -waf-rule-set custom -waf-archive-path /opt/cpguard/app/resources/cpg_modsec_enable.conf.zipIf you wish to enable ModSecurity in Nginx, run the following command
plesk bin server_pref --update-web-app-firewall -waf-rule-engine on -waf-web-server nginx -waf-rule-set custom -waf-archive-path /opt/cpguard/app/resources/cpg_modsec_enable.conf.zipOnce ModSecurity is enabled using one of the above commands, you can turn on cPGuard WAF from Settings.
As mentioned above, you can optionally enable Comodo WAF rules instead of our custom ModSecurity rules set if you prefer to use them as well.
ModSecurity Settings in CyberPanel
You need to go to CyberPanel >> Server >> Security >> ModSecurity Conf and match the settings as given below to enable ModSec Security and logging.
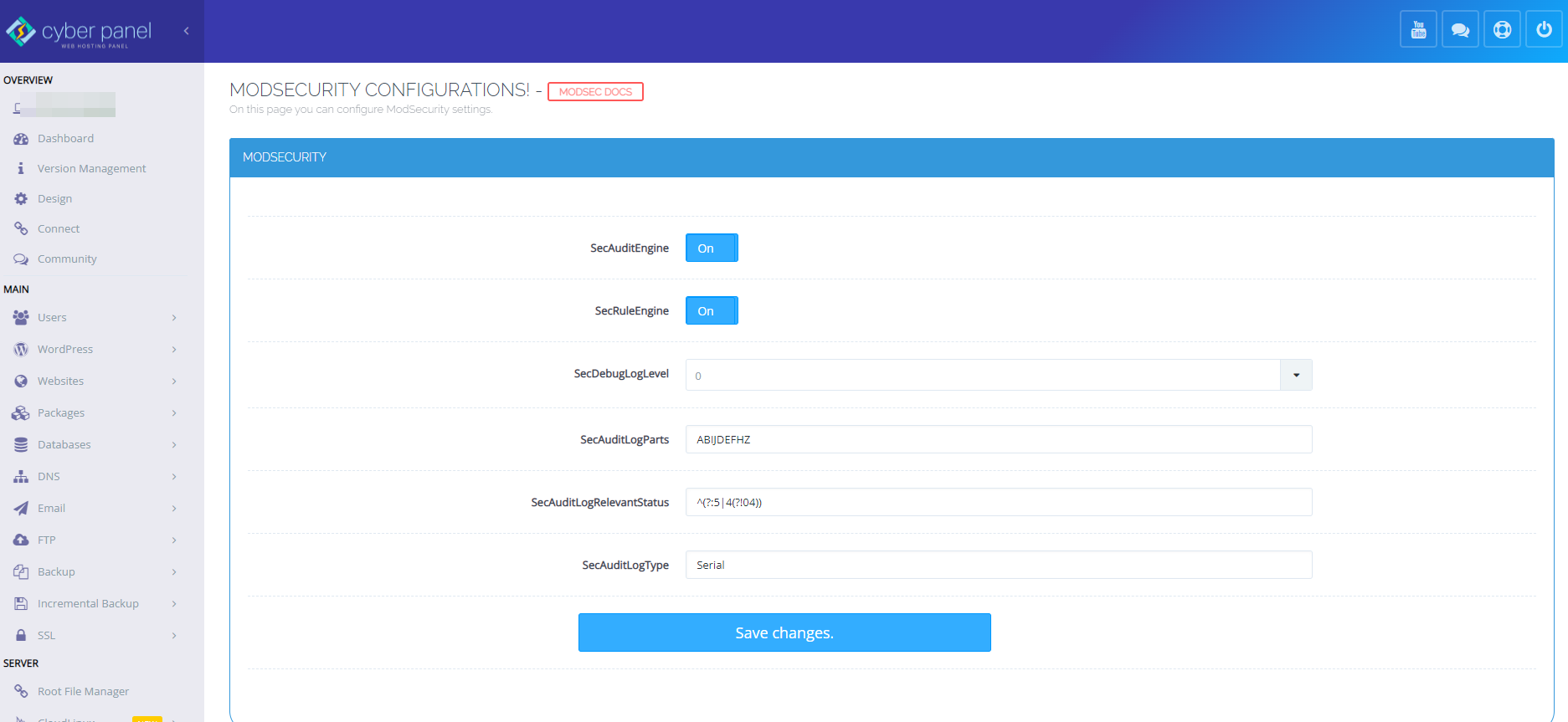
“SecAuditLogParts” value should set to ABIJDEFHZ as per the image above
Also, go to ModSecurity Rule Packs and make sure that “OWASP ModSecurity Core Rules” is NOT enabled as it is not compatible with cPGuard WAF.
Finally, make sure that your server has a fully qualified hostname ( like server.yourdomain.com ) and it should point to your server IP address. This is required to send test attacks to your server and verify the WAF health.
ModSecurity Settings in Control Web Panel [ CWP ]
You have to enable ModSecurity from CWP >> Security >> Mod Security and configure settings like following
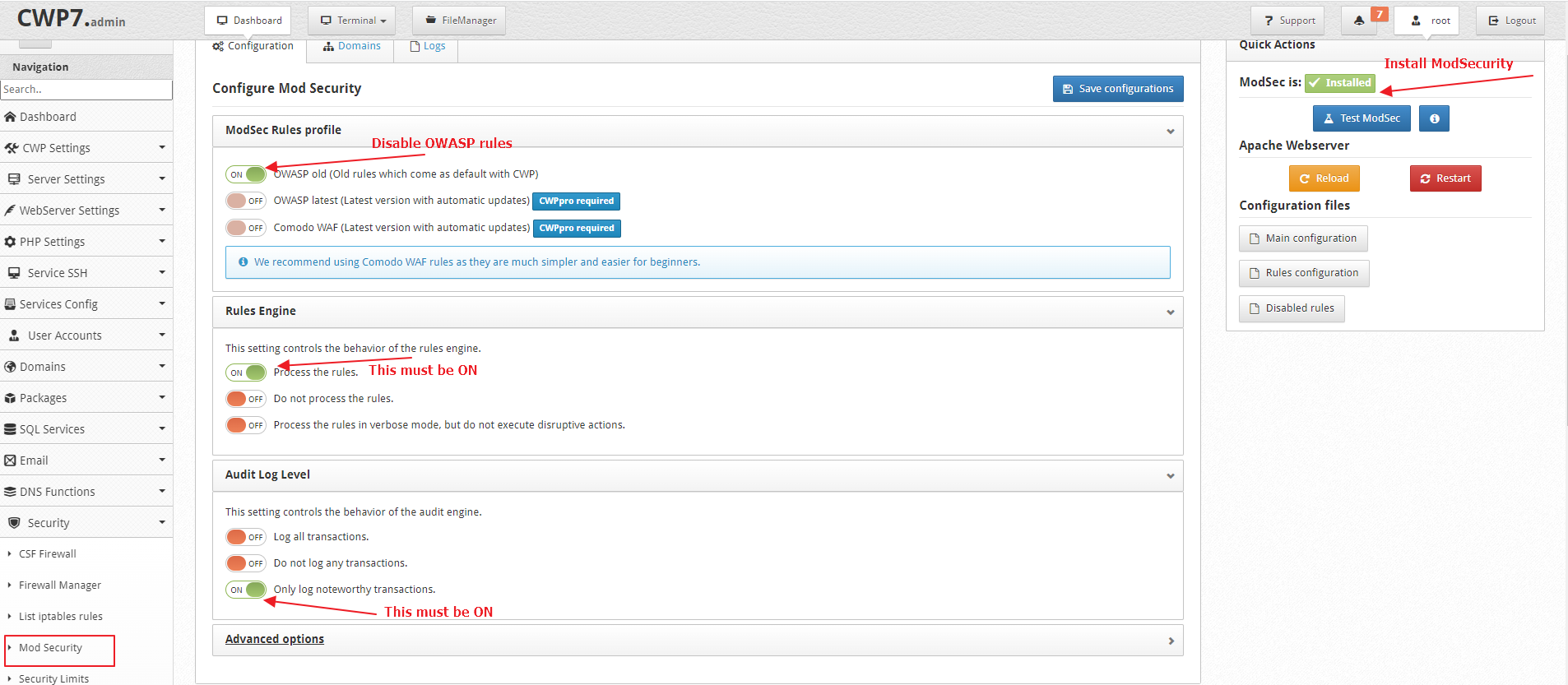
Now edit the Main ModSec Configuration file ( /usr/local/apache/conf.d/mod_security.conf ) from UI or command line and match it like the following
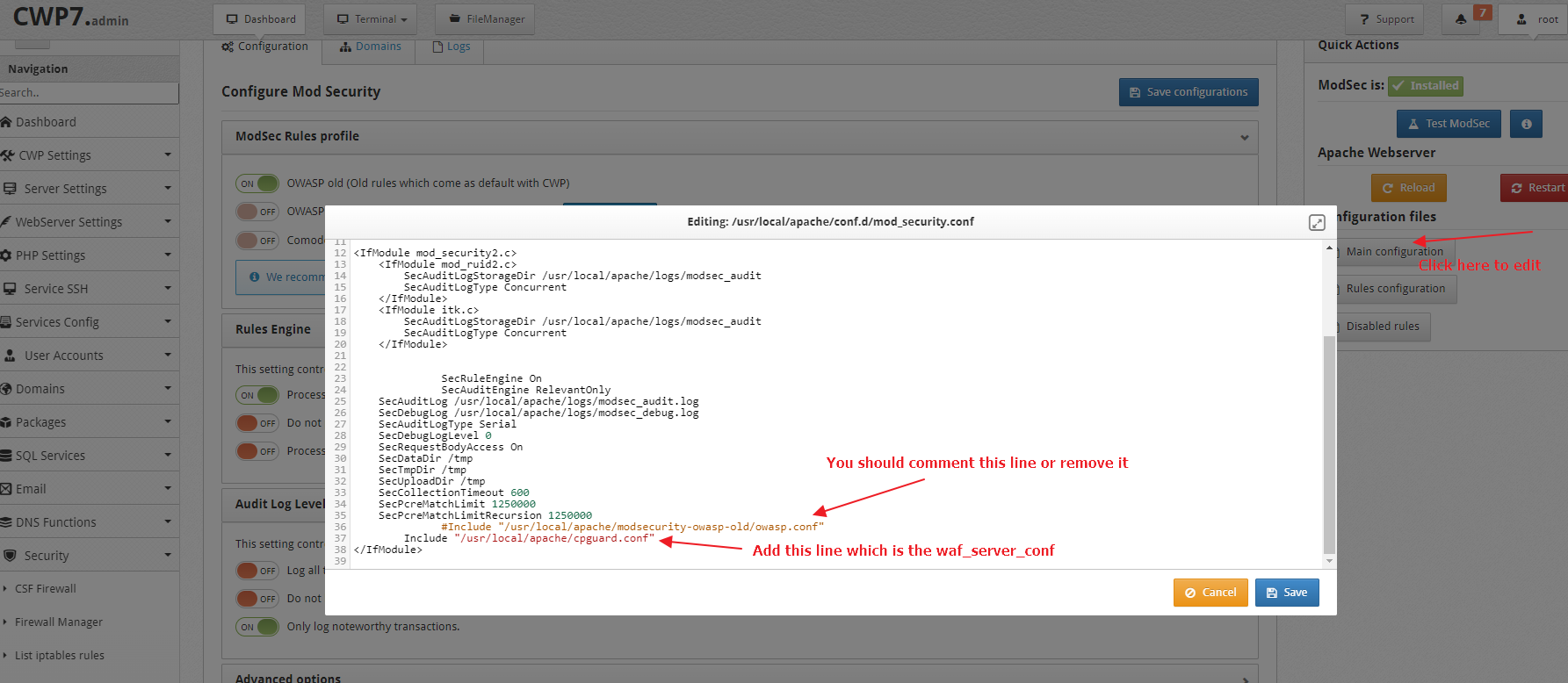
Please refer to CWP Standalone Configuration and complete the configuration once the ModSecurity settings and configured like above.
Settings for Litespeed in Enhance Control Panel
In the LSWS Web Admin console, there is a Web Application Firewall (WAF) section that allows you to enable ModSecurity and add a rule set on an LSWS native server. (For a control panel environment, these steps are unnecessary. Simply enable the ModSecurity rule set from the control panel from Configuration > Server > Security and set the configuration as given below
-
Enable WAF:
Yes -
Log Level:
0 -
Default Action:
deny,log,status:403 -
Scan Request Body:
Yes(If set toYeswill scan post request body) -
Temporary File Path:
/tmp -
Disable .htaccess Override:
Not Set -
Enable Security Audit Log:
Not Set - Enable Security Audit Log:
Native Audit Log -
Security Audit Log:
$SERVER_ROOT/logs/security_audit.log
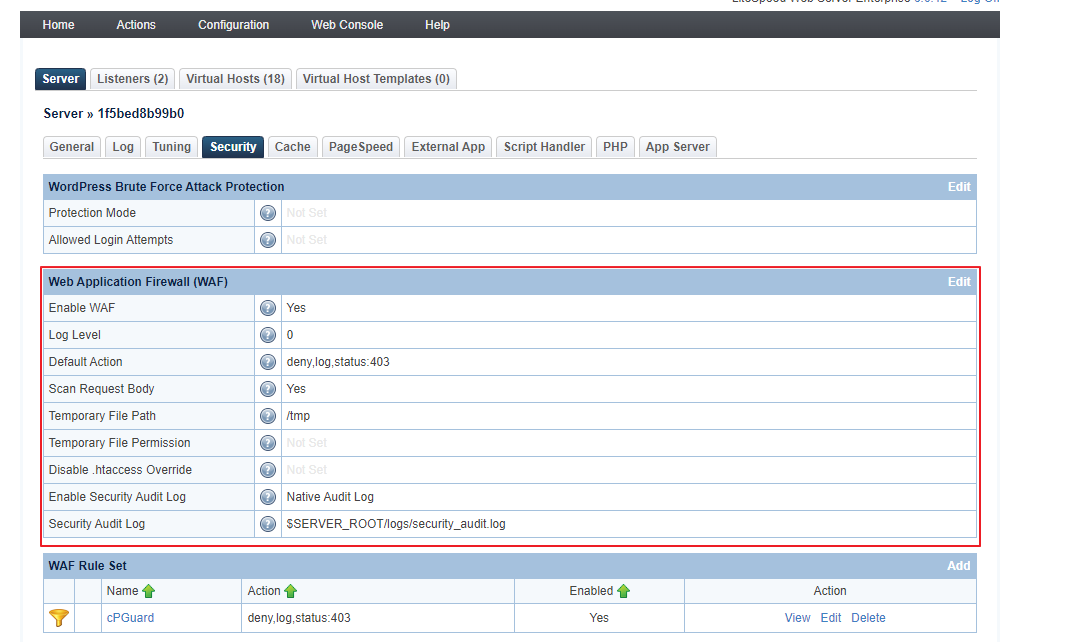
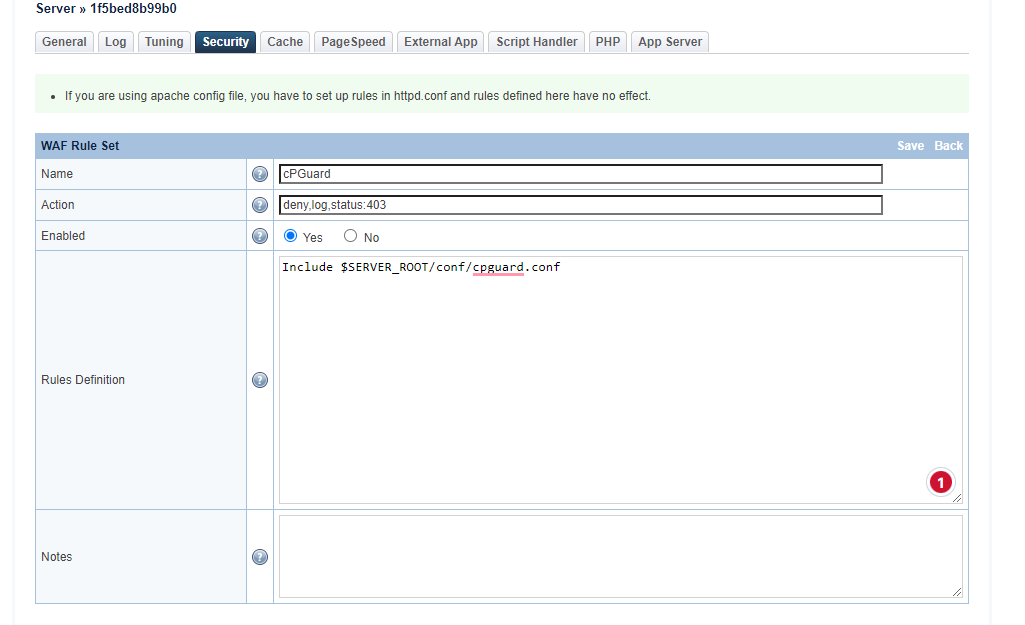
Now add WAF rule set from Configuration > Server > Security > WAF Rule Set > Click on “Add” > use the following values to configure it ( an image reference is given below as well )
-
Name:
cPGuard -
Action: deny,log,status:403
-
Enabled:
Yes -
Rules Definition:
Include $SERVER_ROOT/conf/cpguard.conf
Settings required for Webuzo Control Panel
Webuzo does not enable ModSecurity by default. To enable ModSecurty module in the web server, you need to install one vendor rule. So you can install the OWASP vendor rule which is available by default in Webuzo as per the image below.
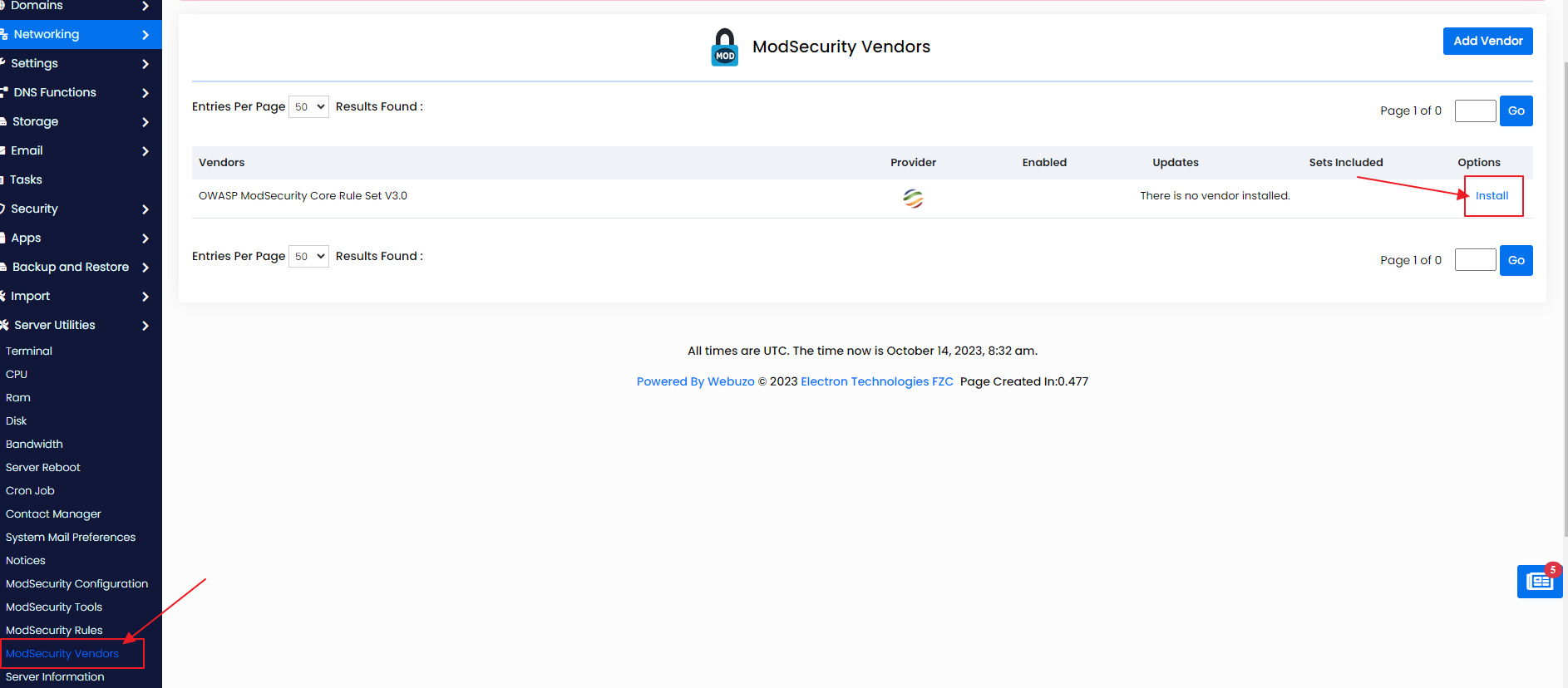
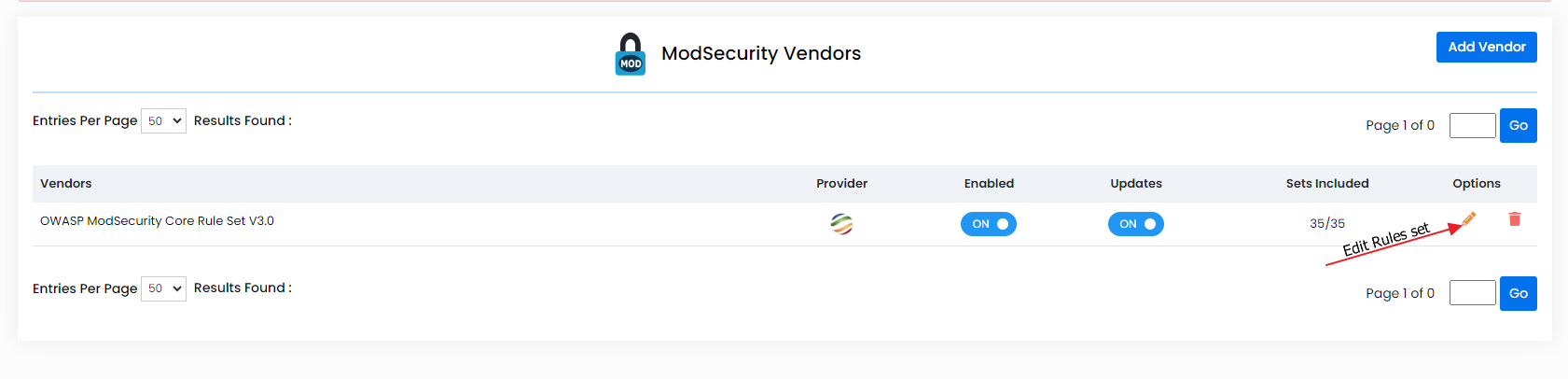
Once OWASP rules set is installed, you need to edit the rules set and disable all rules.
You should not keep it enabled because cPGuard WAF is not compatible with OWASP rules set.
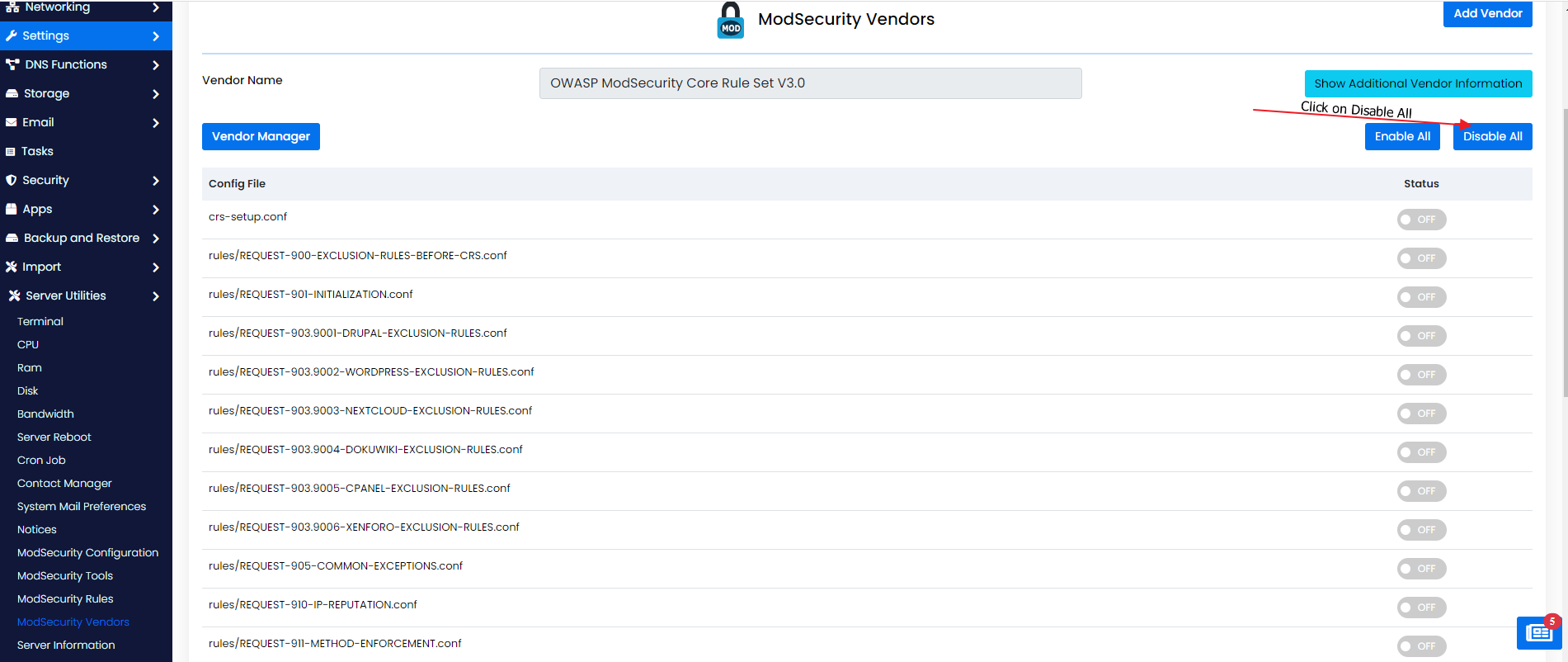
Once this is completed, you can proceed with cPGuard installation and WAF should work fine.
