Web applications must be effectively protected against malware, botnet, and hacker attacks at all times. The Web Application Firewall from cPGuard is based on Malware.Experts commercial rules set with in-house rules from cPGuard to prevent brute-force login attempts against WordPress and Joomla.
WAF RulesSet from Malware.Expert
ModSecurity rules from Malware Expert were built based on intelligence gathered from real-world investigations, penetration tests, and research data in the REAL LIFE environment of over 100000 domains. These rules are developed over ten years with the help of real traffic to websites.
Malware Expert ModSecurity rules provide powerful, real-time protection for web applications and websites running on Apache, and Nginx on Linux Servers with ModSecurity.
Protection
Our rules, provide advanced filtering, security and intrusion protection for PHP applications. Just installing ModSecurity, setup Malware Expert’s rules, and automatic background updates is an effort to promote better security for your services and shared web hosting servers.
Generic Apache and PHP rules, broken out into the following attack categories:
- SQL injection
- Cross-site Scripting (XSS)
- Local File Include
- Remote File Include
- File upload vulnerabilities
- Zero-Day attacks
- Web shells executions
Optimized application specific ModSecurity rules, covering the same vulnerability classes for applications such as:
- WordPress
- Joomla
- Drupal
ModSecurity Rules requirements
- ModSecurity 2.9.x / 3.x and higher (SecRemoteRules)
- Public IPV4/IPV6 address
- Apache, Nginx , OpenLitespeed or LiteSpeed Web Server (LSWS)
Configuring WAF
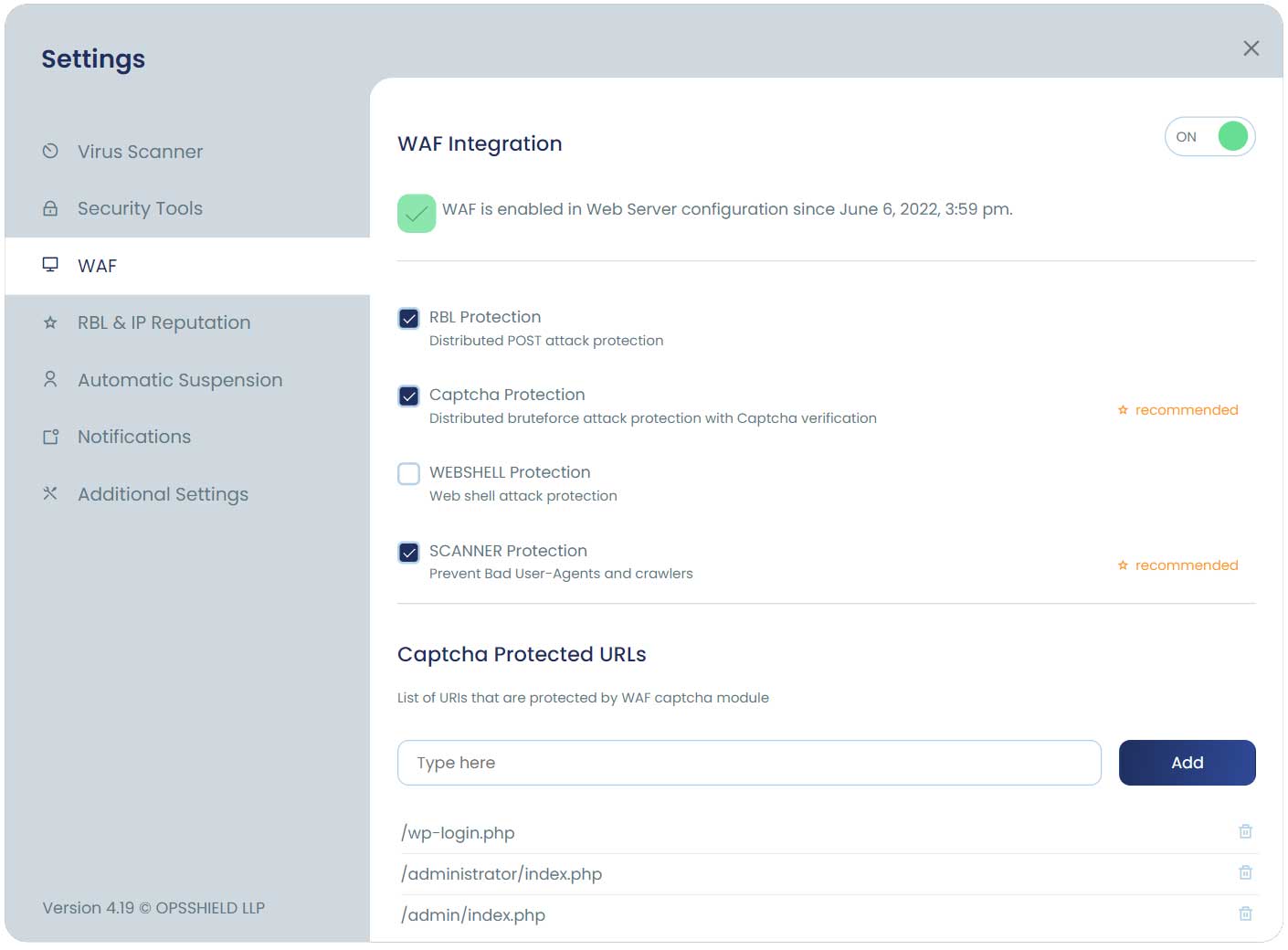
We have multiple sets of rules packaged with the WAF which you can optionally enable or disable along with the core rules. When you enable additional rules, it gives you a higher level of security. However, extra rules may also increase the possibility of blocking some legitimate traffic ( especially RBLand WEB SHELL protection rules set ) due to false alarms. It is likely that you will need to add some whitelist for certain rules IDs which are triggering and cause trouble for your web applications.
We have the following different types of extra WAF rules available for your configuration.
RBL Protection
This provides the advanced DDoS protection for POST attacks [ brute-force, script exploits ] and blocks common abusive IP addresses collected through our network of servers with cPGuard installed.
Captcha Protection
☆ Recommended
This rule set will enforce all users to verify not as bot before accessing the CMS [ like WordPress, Joomla, etc ] login pages or submitting the login credentials. Once they are identified as a real user, they will be able to log in to their website. This can greatly reduce the load due to brute-force attacks. We recommend turning this ON as it can help to block many attacks before reaching your application and helps to reduce server load.
WEBSHELL protection
If you enable this rule set, your server will be protected from the execution of PHP shells like following
- Phoenix WebShell
- FilesMan
- c99shell
- b374k
- WSO
- Ani-Shell
The front page may open in web shells, but command execution [ like a copy, delete, move, etc ] is blocked. You can enable this rules set if you control all the web apps on your server.
SCANNER protection
☆ Recommended
This will help to keep away bad crawlers from your system. This is a major headache for web hosts and causes unnecessary use of system resources. It can block
- Bad User-Agents
- Bad search engine crawlers (Cause High loads)