You can whitelist a WAF rule ID in 3 ways.
1. From WAF Settings
a. Global WAF Whitelist (applies to all domains)
You can add WAF rules to the global whitelist so that they are excluded for all websites on the server.
-
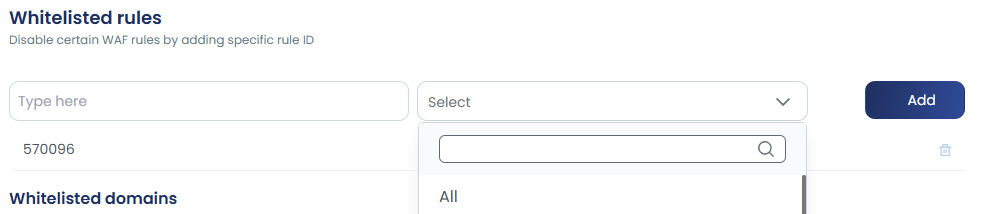
Go to Settings >> WAF & Bruteforce >> Whitelisted Rules.
-
Add the WAF rule ID to the list.
-
Leave the domain selection as “All” or blank to apply it globally.
The CLI commands as follows;cpgcli waf --whitelist --add rule-ID
Add given rule to WAF rules whitelist cpgcli waf --whitelist --remove rule-ID
Remove rule from WAF rules whitelist
b. Domain-Based WAF Whitelist (applies to a specific website)
This allows you to whitelist WAF rules for a specific domain without affecting other sites on the server.
-
Go to Settings >> WAF & Bruteforce >> Whitelisted Rules.
-
Add the WAF rule ID to the list.
-
Select the specific domain from the dropdown.
The CLI commands as follows;
cpgcli waf --whitelist --add rule-ID --domain domain |
whitelisting WAF rules for single domain |
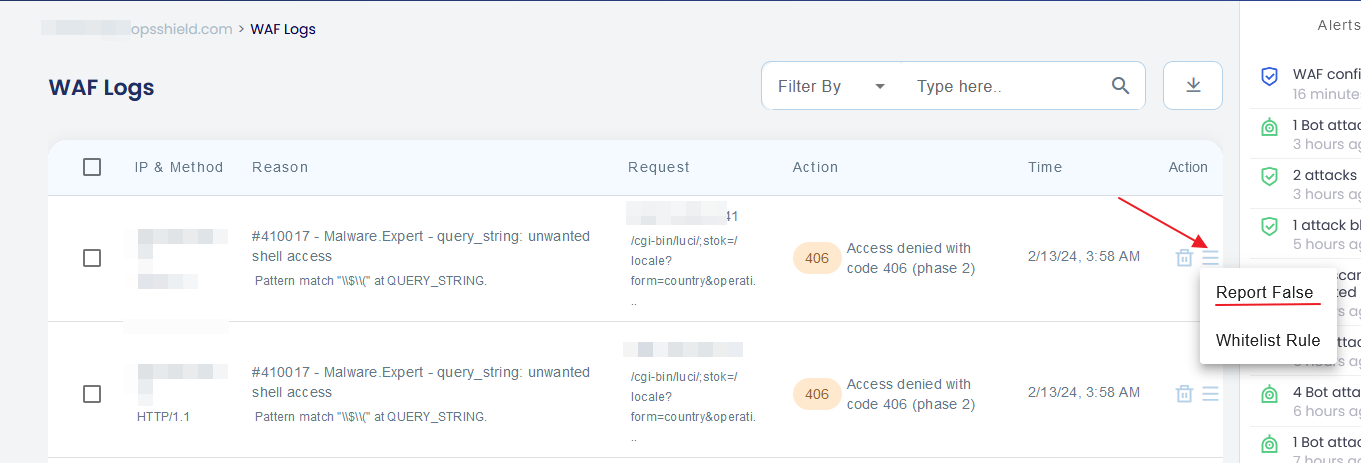
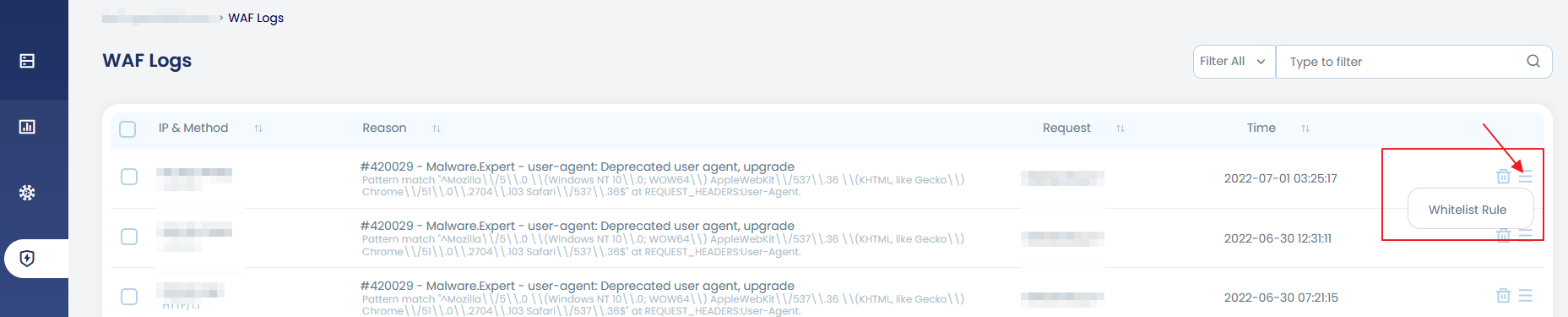
2. From WAF Logs
From the WAF logs page, you can find the option to directly whitelist a rule from the action menu against each entry.
3. Using CLI
You can also use the cpgcli CLI option to quickly whitelist the rule ID from your SSH terminal. Please run “cpgcli -h” for all options available.
cpgcli waf --whitelist --add RuleIDReport a false positive for a WAF Rule Trigger
If you believe that the WAF rule triggered a false positive and the WAF is blocking a legitimate request, you may report it as a false positive. You may do it directly from the WAF logs page. The option to directly report a rule from the action menu against each entry ( refer image below ).